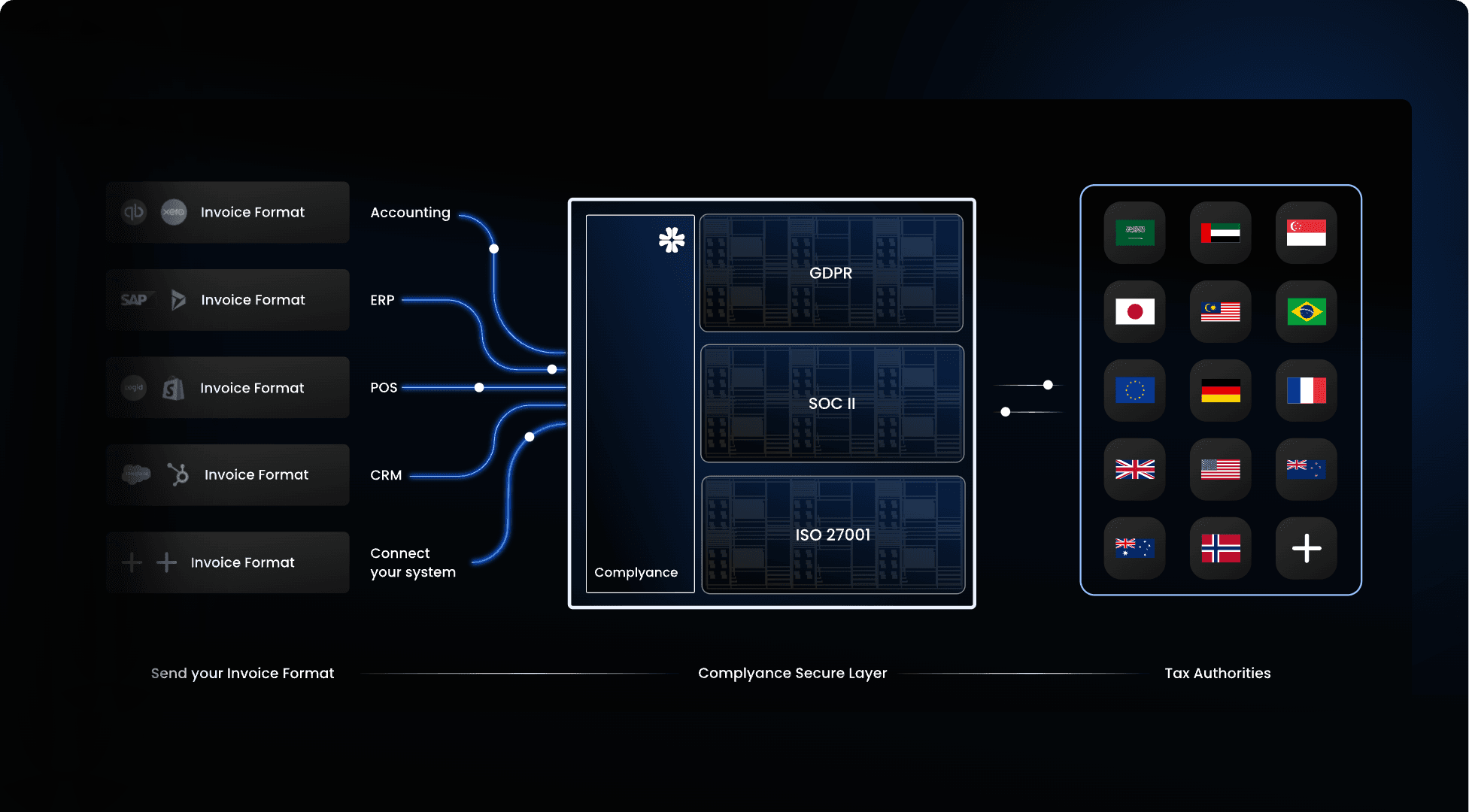
GDPR / PII Handling
Ensure privacy and sovereignty with region-specific PII masking, anonymization, and retention configurations per jurisdiction.
GLOBAL SECURITY STANDARD
Complyance is built from the ground up with security as a first-class principle — from API authentication to access control, audit trails, and encrypted data at every layer.

Security and compliance aren’t bolted on—they’re foundational to how Complyance is built and operated. From encryption to data residency and audit-readiness, every part of our infrastructure is designed to meet the highest enterprise and regulatory standards.
Complyance follows globally recognized frameworks for information security. Our infrastructure is built to meet SOC 2 Type II, ISO 27001, and other enterprise security standards—ensuring trust across every invoice submission.
All data is encrypted using TLS 1.2+ and AES-256 standards, both when stored and during transmission. Your invoice data, payloads, and API responses are fully protected—end to end.
You control where your invoice data is stored and processed. Support data sovereignty and jurisdictional compliance by configuring country-specific or entity-specific storage preferences.
Complyance acts as a secure, intelligent bridge between your billing engine and global tax authorities. From ingestion to validation to submission, every invoice moves through our encrypted layer—ensuring accuracy, traceability, and regional compliance.
Assign granular roles across teams—whether finance, dev, product, or third-party users. Control who can view, edit, submit, or configure based on responsibility.
Track every login, payload update, submission, and change request. Get full traceability for security reviews, audits, or incident response.

Enforce 2FA, manage IP allowlists, set password policies, and restrict access by environment—all from within the Complyance platform.
Complyance gives your security and compliance teams full visibility and control over every invoice interaction—from country-specific data governance to real-time logging and breach readiness. Stay compliant and audit-ready across jurisdictions without sacrificing agility or security.
Ensure privacy and sovereignty with region-specific PII masking, anonymization, and retention configurations per jurisdiction.
Our schema validations, tax logic, and submission flows are updated continuously to reflect every major regulatory mandate—automatically.
Set how long invoices are stored, archived, or purged by country, business unit, or compliance requirement—without developer support.
Every invoice submission is fully traceable, with logs, retries, timestamps, and payload snapshots available for audits or incident reviews.
Keep track of API performance, error rates, country-wise submission health, and uptime metrics with centralized dashboards.
Our platform is structured to support rapid security response—including incident detection, notification workflows, and evidence-ready logging aligned with ISO 27001 and SOC 2.
Support your finance, product, and engineering teams without compromising control. Complyance gives your security team the visibility, policy enforcement, and audit trail needed to meet global standards with confidence.